The locked, the Puzzling & the Declarative
- Assaf Sauer
- Jan 5, 2025
- 3 min read
Updated: Jan 11, 2025

I’ve worked with managed services long enough to have a strong opinion: They’re not my preference. Not because they don’t work—they do. But they come at a cost beyond pricing. They abstract control to the point where architecture, automation, and strategic flexibility suffer.
Yes, some services—BigQuery, fully managed Kafka (e.g., Confluent Cloud)—are harder to replace. But most managed services aren’t essential, just convenient. The question isn’t whether they work, but what you trade off in exchange for that convenience.
The Hidden Trade-Offs of Managed Services
Managed services aren’t just about vendor lock-in. That’s the obvious argument. The deeper issue is that they reshape how you build and operate systems in ways you don’t fully control:
They Define Your Stack, Not You
You’re not choosing the best tool for the job—you’re choosing what the vendor offers.
Need custom tuning, deeper observability, or specialized networking? You’re limited to what’s exposed via their API.
Over time, your architecture becomes dictated by service availability, not engineering decisions.
They Fragment Your Automation
Modern platforms rely on declarative automation (GitOps,K8s manifests..).
Once you introduce managed services, your stack splits—part declarative, part API-driven.
Now, security, CI/CD, and Infra orchestration span across different operational models, increasing complexity instead of reducing it.
They Lock You Into an Operational Model, Not Just a Vendor
The real lock-in isn’t just which cloud you use, but how you operate within it.
Managed services enforce specific IAM models, monitoring systems, and scaling behaviors that don’t translate 1:1 across clouds.
Moving workloads isn’t just about replacing a service—it’s about re-engineering how everything interacts.
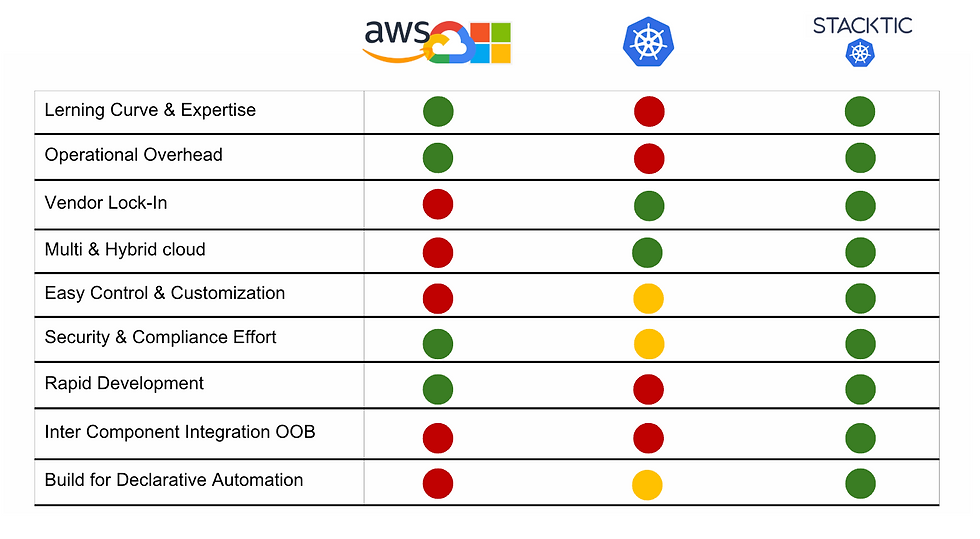
Three Common Architectures and Their Trade-Offs
Full Vendor Lock-In
Everything runs on fully managed services within a single cloud provider.
Works well until you need customization, cost control, or portability—then migration becomes a multi-year project.
Hybrid Approach (Managed Services + Kubernetes)
Popular among companies trying to balance convenience and flexibility.
The challenge? You lose end-to-end automation—your infra now spans Kubernetes and cloud APIs with separate security models, CI/CD pipelines, and operational processes.
Over time, this approach creates friction between automation layers and increases operational/Security complexity instead of reducing it.
Pure Kubernetes-Native
The most agnostic and automated approach, but requires more expertise.
The only setup where you can deploy an entire full-stack system with a single command, independent of the underlying cloud.
Less popular due to skill gaps, but the only path to true portability, control, and long-term efficiency.
The Real Choice: Control vs. Convenience
Managed services make life easier today, but they shape your architecture in ways that limit long-term flexibility. Native Kubernetes gives you full-stack automation, cloud portability, and deeper control, but demands stronger expertise.
Stacktic as an example
Stacktic runs as a SaaS solution, but I deploy it like a true full-stack system—whether staging, private test environments, or on-demand on any cloud. With one command, I spin up Full-Stacks on GKE, AKS, or on-prem per customer needs.
But if I replace MongoDB with DocumentDB or PostgreSQL with RDS, here’s what breaks:
1. Deployment & Security Automation
Managed services require manual API-based provisioning, disrupting my declarative CI/CD and automation workflows.
Security enforcement is fragmented—now I need to manage Kubernetes RBAC and OPA policies separately from cloud IAM and security roles.
2. Networking & Security Complexity
No longer just Kubernetes-native networking—now I must configure firewalls, VPC peering, and cloud IAM policies for DB access.
TLS and authentication are no longer controlled inside Kubernetes, but split across cloud-specific security layers.
3. Observability Breaks in Two
Log aggregation becomes fragmented—Loki handled everything before, now I need CloudWatch, Azure Monitor, or Stackdriver.
Metrics and tracing are split—Prometheus covers Kubernetes, but now I need cloud-native monitoring tools for managed services.
Alerting is no longer centralized, requiring additional integrations.
4. Cloud Lock-In & Portability Loss
My stack is no longer fully portable—I can’t deploy the same way on-prem or in another cloud.
Vendor-specific IAM and networking constraints make migrations difficult.
5. IaC Overhead & Fragmentation
Now, Terraform, Pulumi, or Crossplane is required to manage cloud services alongside Kubernetes YAMLs, adding complexity.
Instead of a single GitOps pipeline, I now need separate provisioning workflows for Kubernetes and cloud APIs.
6. Increased Operational Overhead
Backups, scaling, and performance tuning depend on cloud provider policies, limiting flexibility.
IAM and access control require syncing cloud roles with Kubernetes RBAC, increasing security risks.
The Trade-Off: Flexibility vs. Lock-In
Managed services fragment automation, security, and observability, forcing extra layers of networking, IAM, and tooling overhead.
By staying Kubernetes-native, Stacktic ensures true automation, portability, and full-stack control—on any cloud or on-prem.
One of Stacktic’s core goals is to simplify modern application deployment on Kubernetes while remaining open, flexible, and free from vendor lock-in or opinionated technology constraints. With Stacktic, you don’t need Infrastructure-as-Code (IaC)—everything is fully automated, letting you focus on innovation instead of managing infrastructure.
.png)
.png)


Comments